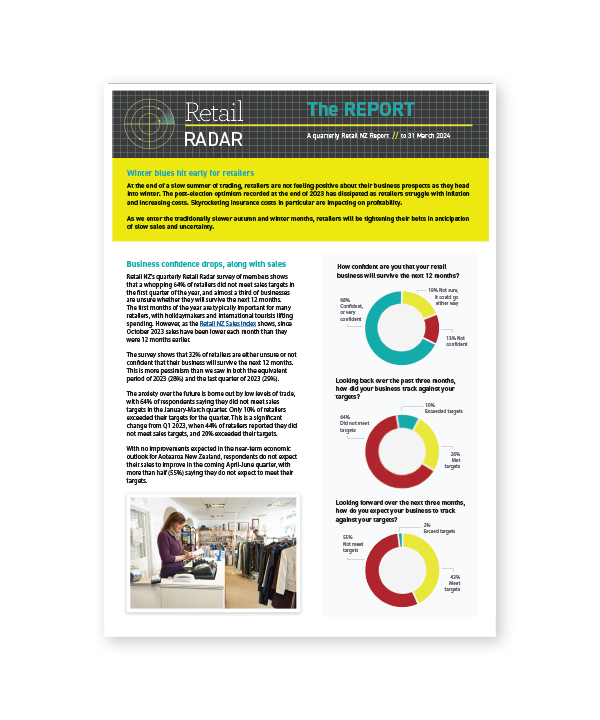
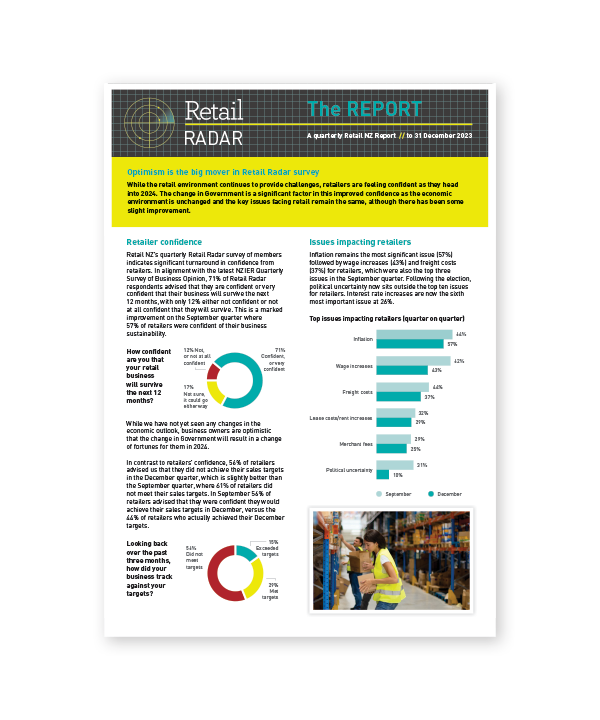
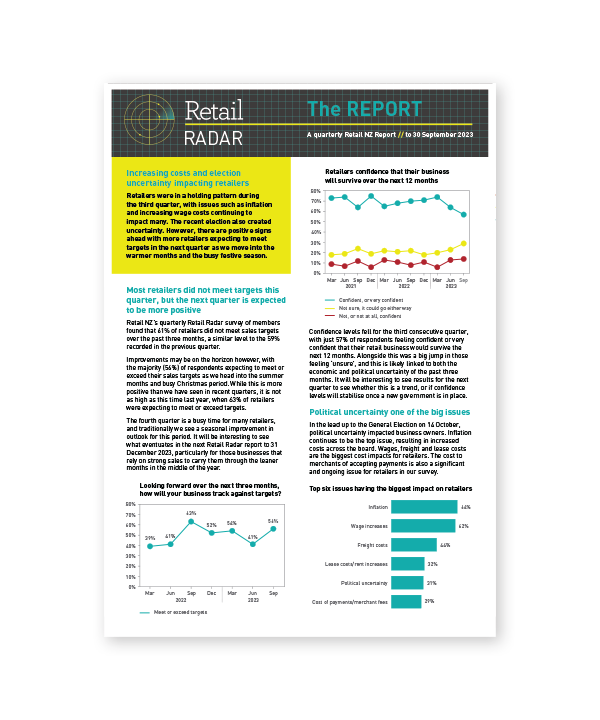
Every year there are three and a half days that most stores must close under the Shop Trading Hours Act 1990. Learn more about these days.
What does Retail NZ do for business owners?
Retail NZ is here for you. With us, you’ll get the latest business updates, advice, advocacy, financial savings, upskilling and insights. If you’re looking for guidance or support, ask us first! We’re New Zealand’s peak body for retailers.
Vibrant high streets, welcoming town centres and engaged ecommerce businesses are at the hearts of our communities. Develop and prosper with Retail NZ, your professional support network.
JOIN US, and start making the most of your membership today!
Got questions? You can contact us on 0800 472 472 or [email protected], or 1800 128 086 freephone from Australia.
Need to know how to pay your employees for public holidays in 2024? You're in the right place!
Here's what you need to know about the current Minimum Wage rates in New Zealand, what it means for your employees, and your retail business.
We speak up for retailers, and elevate the voice of retail. Here you can see Retail NZ’s latest commentary in news and media.
Some very interesting facts about retail as a sector in New Zealand and what does it represent. You might not want to miss.
Retail NZ represents the retail sector in the media. Check out our latest appearances in the news!
Most Popular
Our great friends at Westpac offer Retail NZ members discounts on credit card merchant fees. Our longstanding partnership with Westpac has seen the support of the NZ retail industry. Find out more...
Drive your business further with Z Business Partner. Say "hello" to Z Business Partner – a fuel programme that’s a big plus for your business.
What are Meridian’s benefits for Retail NZ members? Join Meridian today on a two year Fixed Energy Plan, and as a Retail NZ member, you’ll get a welcome credit of up to $600*.